Decentralized and Verifiable Randomness in ICP: Leveraging Threshold Cryptography for Fairness and Security
ICP's threshold cryptography ensures secure, unpredictable randomness for decentralized applications, overcoming traditional blockchain vulnerabilities in fairness and verifiability.
Key Takeaways
True Decentralization, No Middlemen: ICP’s on-chain randomness eliminates reliance on third-party services like Chainlink VRF, offering fully decentralized, trustless, and cost-effective randomness generation.
Unpredictable, Tamper-Proof Randomness: By using Threshold BLS Signatures and Verifiable Random Functions (VRFs), ICP ensures randomness that’s provably unpredictable and verifiable.
Essential for Next-Gen DApps: Gaming, lotteries, NFT generation, and DAO governance all benefit from ICP's transparent, on-chain randomness, leading to fairer, more trustworthy applications.
Mitigates Exploitation & Bias Risks: Unlike traditional blockchains where miners can manipulate timestamps or block hashes, ICP’s randomness is finalized only after block confirmation, making it immune to manipulation.
Catalyst for DeFi, Gaming, and AI Innovation: Projects like World Lottery and dynamic NFTs showcase how ICP’s randomness supports innovation and drives new use cases for decentralized applications.
Solving the Blockchain Randomness Problem: ICP’s randomness system addresses blockchain predictability, ensuring that neither miners nor validators can pre-compute or influence random outcomes.
What is Randomness
Randomness refers to the absence of any pattern or predictability in a series of events. In our everyday lives, rolling dice or flipping a coin are simple examples of randomness. However, in the world of computing and blockchain, generating true randomness is much more complex. It’s not enough for something to “seem random”; it must also be provably unpredictable and secure.
Randomness is a crucial pillar of blockchain and cryptography. It enables secure key generation, random selection of validators, lottery draws, NFT attributes, and more. Without reliable randomness, decentralized systems would be vulnerable to exploitation and manipulation. The main random number application scenarios include:
Key Generation: Cryptographic keys used for encryption and decryption must be unpredictable. If the randomness behind key generation is weak, attackers can predict and compromise the keys.
Consensus Mechanisms: Randomness is used to randomly select block validators or leaders in certain blockchain consensus protocols, ensuring fairness and decentralization.
Gaming and Lotteries: On-chain games and lottery draws rely on randomness to ensure fairness. If the randomness can be predicted or controlled, it would give certain players an unfair advantage.
NFT Generation: The attributes of some NFTs are randomly assigned, and fair randomness ensures that all participants have an equal chance of obtaining rare items.
Pseudorandom Numbers in Blockchain
A closely related concept is pseudorandomness, which refers to random numbers that are generated by algorithms. Most PoS blockchains, including Ethereum 2.0, use pseudorandom numbers (PRNs) rather than true random numbers. The main reasons for this choice lie in the nature of blockchain systems and the requirements of decentralization, efficiency, and verifiability.
Decentralization and Trustlessness
True randomness is often generated using specialized hardware (like hardware random number generators) or external randomness providers, which introduces a reliance on external entities. This reliance goes against the principles of decentralization in blockchains.
By using pseudorandom numbers generated through on-chain methods like RANDAO, Ethereum 2.0 ensures that no single participant or third party has control over the process.
Verifiability and Transparency
True randomness is difficult to verify without introducing an additional trusted party. Blockchain participants need to be able to independently verify the randomness.
Pseudorandom numbers generated via methods like RANDAO or VRF are fully verifiable on-chain. Anyone can see and verify the process used to generate the number, which enhances transparency and trust.
Performance and Efficiency
True random number generation requires more computational resources and specialized hardware, which can slow down blockchain operations.
Pseudorandom numbers are computationally cheaper to generate on-chain, allowing for faster and more efficient block production and consensus.
Pseudorandom numbers play a crucial role in mainstream blockchains like Ethereum 2.0. However, the decentralized nature of these networks introduces unique challenges in generating randomness. While pseudorandom numbers may appear random, they are technically generated from a specific seed or initial value. This means that if the seed is known, the sequence of numbers can be reproduced. Traditional methods, such as relying on block hashes, are often vulnerable to manipulation.
Methods for Generating Randomness in DApps
DApps, especially in use cases like lotteries, NFT generation, and gaming, need to leverage randomness in a decentralized, verifiable, and tamper-proof manner. Pseudorandom numbers are widely used in blockchains because their generation methods allow traceability and verifiability—critical features for decentralized environments. Below are three primary methods DApps can use to generate randomness, each with its own advantages, limitations, and applications.
Approach 1: Using Oracles (Off-Chain Randomness)
Oracles like Chainlink VRF (Verifiable Random Function) provide off-chain randomness to smart contracts. Chainlink VRF generates a random number off-chain using a cryptographic function and returns it to the blockchain along with cryptographic proof.
The smart contract can verify this proof to ensure the randomness was not tampered with by the oracle, ensuring trust and transparency.
Benefits
High Security: The randomness is generated using cryptographically secure methods.
Verifiability: Smart contracts can independently verify the validity of the randomness using the accompanying cryptographic proof.
Unpredictability: No participant (including the oracle) can predict the result beforehand.
Challenges
Trust Assumptions: While verifiable, users must still trust the oracle service.
Cost: Relying on off-chain oracle services incurs gas fees and service fees.
Approach 2: Leveraging Pseudorandomness in blockchain
This approach uses the inherent randomness within blockchain data, such as block hashes, timestamps, or validator selections, as a source of randomness.As mentioned earlier, obtaining pseudorandom numbers directly using this method are often vulnerable to manipulation. To address this, mainstream blockchains like Ethereum 2.0 employ more sophisticated randomness generation mechanisms. Ethereum 2.0 use RANDAO, a collaborative randomness scheme where validators contribute individual random values. These values are aggregated into a final random number.
Benefits
Decentralization: No need for external service providers (like oracles) to generate randomness.
Cost-Effective: Since randomness is derived from existing blockchain data, no additional fees are required.
Availability: Every validator or miner can participate in randomness generation.
Challenges
Predictability: If validators can see incoming random values before submitting theirs, they may strategically withhold or influence the final randomness (the “last-revealer” problem).
Exploitation Risk: Miners or validators might manipulate block hashes to achieve a favorable outcome in random draws.
Approach 3: On-Chain Randomness Using Smart Contracts
Smart contracts can generate randomness by using blockchain-specific data, such as block hashes, timestamps, or even transaction hashes. The contract takes this data as input and applies hashing functions (like Keccak-256) to produce a random value.
Benefits
Simplicity: No need for off-chain services or participant contributions.
On-Chain Verification: The randomness is transparent and can be verified directly on-chain.
Low Cost: Smart contracts generate randomness using existing blockchain data, so there are no extra service fees.
Challenges
Trust Assumptions: More complex for devs and may introduce trust assumption.
Pseudorandomness within Blockchain
The ideal method for obtaining randomness for DApps should optimize leveraging pseudorandomness within blockchain. It must avoid introducing new trust assumptions or relying on third-party services, ensuring strong decentralization, cost-effectiveness, and verifiability. Additionally, it should mitigate exploitation risks and predictability, guaranteeing that the randomness generation process remains unpredictability, tamper resistance and verifiability.
While in systems where randomness plays a significant role, nodes and validators can use the deterministic nature of randomness generation to their advantage:
Randomness often depends on inputs such as block hashes, timestamps, or cryptographic signatures.
Miners can calculate the pseudorandom outcome tied to their block before broadcasting it. If they dislike the result, they may withhold the block to allow another miner to produce a block with a different random seed.
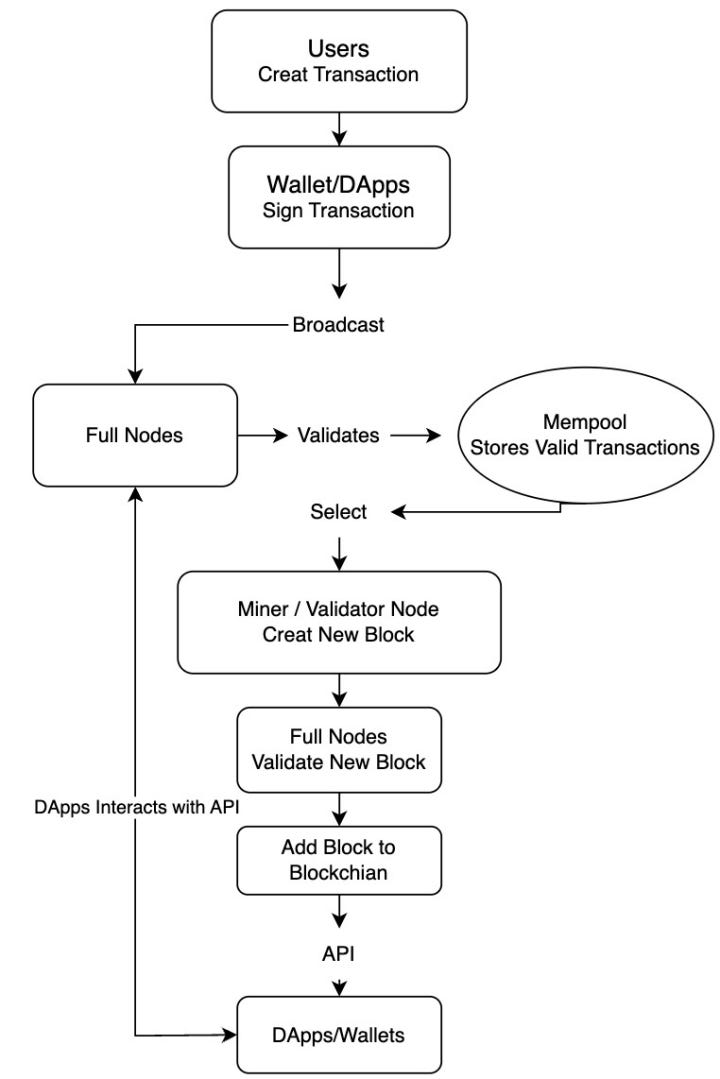
Let's start at the very beginning and discuss how this happens from blockchain (in Ethereum's case) with transaction signatures on the chain.
The brief flowchart of message passing as below. Message passing involves the communication between different components of the blockchain network, including nodes, users, and external services. When a user initiates a transaction via a wallet or front-end application, the transaction data is passed through APIs to the network.
Based on the flowchart, the process can be divided into five stages, each with potential implications for the transparency, unpredictability, and manipulability of randomness in a PoS blockchain. Let’s discuss each stage in detail:
Transaction Creation and Signing
Transactions are created and signed by users (EOA accounts) or wallets like MetaMask. During this stage, the user generates a transaction locally in their wallet, which might involve actions like transferring funds or calling a smart contract.
When signing a transaction, the user’s private key is used to sign transaction data (e.g., destination address, amount, nonce) through cryptographic algorithms such as ECDSA. These algorithms depend on a random private key or a local random number for signature generation.
Since the randomness here is generated locally on the client-side, block producers have no influence over this process.
Transaction Broadcasting and Propagation
Signed transactions are broadcast across the P2P network and received by nodes, where they are placed into mempools.Validators collect these transactions from the mempools to decide which ones to include in the next block.
The broadcasting stage does not rely on randomness, as nodes act merely as intermediaries relaying transactions across the network.
Transaction Collection and Ordering
Validators pick transactions from the mempool and determine their order in the block. Validators may intentionally manipulate transaction order, such as through Maximum Extractable Value (MEV), to prioritize transactions that benefit themselves.
While this process involves discretion by validators, it reflects deliberate selection rather than true randomness.
Block Proposal and Creation
Validators, acting as block producers, create blocks and have control over timestamps, transaction ordering, and block hashes. These elements can serve as randomness inputs in decentralized applications (DApps).
Block Timestamp: Though timestamps are monotonically increasing, validators can adjust them slightly (e.g., ± a few seconds). This may influence certain on-chain behaviors, such as those relying on time-based randomness (e.g., generating NFT traits based on block.timestamp).
Transaction Data and Hash: Some DApps, such as blockchain-based lotteries, use values like block.hash, block.timestamp, or block.number as randomness sources. Block producers can partially control these values.
Block Hash: The block hash is derived from hashing the block header, which includes components such as the timestamp, Merkle root, and transaction order. Validators can adjust these inputs (e.g., transaction sequence or timestamp) to influence the resulting block hash, thereby impacting randomness outcomes for applications relying on it.
Block Validation and On-Chain Confirmation
After a block is created, it is validated and confirmed by the network’s validators and nodes.
At this stage, the block’s randomness sources, including hash and timestamp, are finalized and immutable. Any randomness derived from these elements is set, and further manipulations are impossible
Judging from the above process, block producers can foresee pseudorandom outcomes in specific blockchain designs (through data in Mempool) due to the deterministic nature of many cryptographic and computational processes used to generate randomness . In many blockchains, pseudorandom values are derived from deterministic inputs available within the blockchain system. Input seeds include:
Block Hashes: The hash of a block or a previous block is often used as a seed for randomness. Since miners generate the block and compute its hash, they can predict the outcome.
Transaction Data: Specific transaction details (e.g., timestamps, addresses) might be used as input. If a miner includes these transactions in their block, they can predict the randomness derived from them.
Cryptographic Signatures: PoS blockchains may derive randomness from digital signatures or similar cryptographic data. A block creator who signs the block can compute and foresee the pseudorandom outcome.
If the outcome is unfavorable, they might choose to re-sign the block with different data or refuse to publish it, retrying with a better configuration. Detail behaviors as bellow:
Withholding Blocks:
Block creators can evaluate the pseudorandom outcome derived from their block (e.g., by hashing or including specific data).
If the outcome is unfavorable to their interests (e.g., losing a bet or negatively impacting a stake selection), they may choose not to publish the block.
This creates a situation where only favorable blocks are propagated to the network.
Injection of Bias:
A node can selectively craft transactions or data inputs included in their block to influence the pseudorandom outcome.
For example, in Proof-of-Stake (PoS) blockchains, the randomness seed might derive from signatures, hash values, or other deterministically derived data, allowing attackers to tailor blocks.
Collusion:
Multiple nodes controlled by a single entity or a coalition of entities can coordinate to selectively propagate or discard blocks, amplifying their ability to bias the randomness.
Innovative Randomness System on The Internet Computer Protocol
ICP’s randomness system, built on Threshold BLS Signature Schemes, brings a game-changing innovation. It also employs a Verifiable Random Function (VRF) to generate randomness tied to specific consensus rounds.
How Does It Work?
In the Internet Computer Protocol, randomness is generated through a decentralized and cryptographically secure process that ensures fairness and trustworthiness. At its core, this mechanism relies on a VRF, which produces random outputs deterministically tied to specific inputs. The VRF ensures that these outputs are unpredictable, tamper-proof, and verifiable, making them ideal for use in decentralized applications.
The process of randomness generation is closely integrated with the network’s consensus mechanism. During each round of consensus, subnet nodes collaboratively generate randomness. Each node computes a partial signature using its private key, and once a sufficient number of nodes (meeting the threshold 2/3) contribute, these partial signatures are combined into a single threshold signature. This threshold signature is then hashed to produce a random value that is cryptographically tied to the current round and consensus state. This ensures the randomness is unique and decentralized, eliminating any reliance on a single point of trust.
The randomness generated is encapsulated in a "random beacon," which serves as the seed for a pseudorandom number generator (PRNG) called the "random tape." This random tape produces unique random values for smart contracts (canisters) that requested randomness in the previous round. Random values in random tape can not be seen until the block is finalized. By tying the output to the next consensus round, ICP prevents the possibility of current randomness being used to predict future outputs, thus enhancing the security and integrity of the system.
Developers access this randomness through APIs provided by the management canister or programming modules like Motoko’s Random module. The process is asynchronous, aligning with the network’s consensus rounds.
For example, in Motoko, a developer can simply call a function to fetch randomness tied to the current round for use in their application. This ensures that smart contracts can incorporate secure randomness in a straightforward and efficient manner.
For a simplified overview of the above process, the main process of ICP's random number generation on chain is as follows:
Node Contributions: Subnet nodes independently generate cryptographic shares using threshold cryptography. These shares collectively represent a shared secret (randomness), with fault tolerance for some malicious nodes.
Threshold Signature Creation: When a sufficient number of nodes (e.g., two-thirds) contribute, their shares are aggregated into a threshold signature, forming the core randomness value.
Random Value Generation: The threshold signature is hashed to produce a decentralized random value. This value is encapsulated in a random beacon, which ensures it is unpredictable and tamper-resistant.
Integration with Consensus and Random Tape:
The random beacon serves as the seed for a pseudorandom number generator (PRNG) called the random tape.
The random tape produces unique random values for canisters (smart contracts) that requested randomness in the previous round. These values are concealed until the block is finalized, preventing tampering or exploitation.
Tying random value outputs to the next consensus round ensures current randomness cannot predict future outputs, enhancing security and integrity.
Public Release: The generated randomness is published on-chain as part of the random beacon, allowing anyone to verify and use it transparently.
This decentralized approach eliminates reliance on off-chain randomness providers, and ICP leverages threshold cryptography to generate randomness in a decentralized and secure manner. Key aspects include:.
Non-Predictability: Randomness is derived from threshold signatures created by the network’s subnet nodes. Since these signatures are the result of cryptographic aggregation, no single node can predict or control the output.
Collective Agreement: Randomness is a product of the agreement among a subset of nodes in a subnet. This ensures that no single entity can bias the random output.
Tamper Resistance: The cryptographic process ensures that the randomness cannot be manipulated by any single node or colluding subset of malicious nodes below the fault tolerance threshold.
How Dapps Leverage The Unique Technology
ICP's randomness mechanism is central to its design for scalability, security, and decentralization, providing unpredictable and verifiable random values to support various applications and consensus mechanisms.
Unlike Ethereum Ecosystem, which relies on block hashes or external oracles (e.g., Chainlink VRF) for randomness, ICP’s approach is native, decentralized, and cryptographically secure. This avoids introducing third-party dependencies or vulnerabilities tied to on-chain determinism.
The randomness generated by ICP finds application in various domains:
Dynamic NFTs and Gaming
Imagine games where loot drops are transparently random, or NFTs whose attributes evolve unpredictably. ICP’s randomness provides the perfect backbone for these next-gen applications.Prediction Markets and DeFi
In prediction markets, randomness can be used to settle disputes or handle edge cases fairly. Similarly, DeFi platforms can leverage randomness for randomized rewards or governance decisions.Governance in DAOs
Randomness enables fair allocation of voting rights or determines proposal priorities, enhancing the transparency and efficiency of decentralized governance and ensures fair, unpredictable staking rewards.AI and Randomness
The combination of AI and blockchain randomness is a frontier with immense potential. Here’s how they might integrate:
Dynamic AI Models
AI-driven agents could use randomness to make decisions more robust and less predictable, such as in dynamic pricing or resource allocation.Fair Dispute Resolution
When AI models reach conflicting conclusions, randomness can introduce a neutral mechanism for arbitration, ensuring fairness.Autonomous Systems
Chain-based AI systems could utilize randomness to introduce variability in behavior, making them more versatile in complex environments.
Conclusion
ICP’s unique randomness mechanism, rooted in threshold cryptography, offers a secure, decentralized, and verifiable solution that enhances trust and efficiency. Its design aligns well with the protocol's broader goals of scalability, high performance, and fair participation, setting it apart in the blockchain ecosystem. Of course, we also see the challenges like fault tolerance which requires a minimum number of honest nodes in a subnet to maintain security.