Self-Sovereign Identity: A Decentralized Identity Technology Shaping Identity Security
The future of digital identification is decentralised. Self-sovereign identity solutions will transform the way we interact online.
Takeaways:
Centralized systems currently face privacy and security issues in solving the internet's identity challenges. SSI addresses these concerns by leveraging decentralized technologies like blockchain and cryptography, giving individuals full control over their digital identities.
Decentralized Identifiers (DIDs) play a crucial role in Self-Sovereign Identity (SSI) by allowing users to own and control their digital identity. They leverage cryptographic key pairs and are built on distributed ledger technology, enabling secure, verifiable, and privacy-respecting identity management without relying on centralized authorities.
The traditional Identity and Access Management (IAM) market and the SSI market are both expanding, but the dynamics between them show a significant shift. The traditional IAM market is larger, but SSI is expanding rapidly due to its efficiency, enhanced user experience, resistance to data surveillance, and support for individual control over personal data.
The business model of SSI in Web3 centers around decentralized identity solutions that empower users to control their data while offering verifiable credentials for various applications. Revenue streams include charging for verifiable credential issuance, credential verification services, subscription-based identity management platforms, consulting services for integration, transaction fees in identity marketplaces, and privacy tools.
Major blockchain platforms are actively developing their own SSI systems or projects, each aligning with the core principles of Self-Sovereign Identity (SSI).ICP's (Internet Computer) Internet Identity (II) is a decentralized solution aligned with SSI principles, offering secure, passwordless authentication via device-based keys and blockchain. Its strengths include strong security and user control, but challenges like cross-platform compatibility remain. Despite this, II is positioned to play a key role in decentralized identity systems.
Introduction
The internet, as originally designed, lacked a built-in identity layer, which has led to significant challenges in verifying the authenticity of individuals and organizations online. Kim Cameron, Chief Architect of Identity at Microsoft, highlighted this issue by noting that the internet’s underlying TCP/IP protocol only identifies the address of the machine being connected to, without providing any information about the person or entity controlling it. This gap has left users vulnerable to impersonation, fraud, and data breaches, as there is no inherent mechanism to verify who is on the other end of the connection.
Recently, the newly proposed “Cybersecurity ID” by the Chinese government has raised widespread controversy. Individuals can obtain a "Cybersecurity ID" through the National Network Identity Authentication app by uploading their ID card, scanning their face, and linking their phone number. While the government intended to safeguard privacy and combat online fraud by the approach, the centralized models raise concerns about privacy, security, and the potential misuse of data by authorities or corporations. Users have limited control over their personal information, creating vulnerabilities that are increasingly exploited in the digital age.
Self-Sovereign Identity (SSI) offers a transformative solution to these challenges by enabling a decentralized, user-controlled approach to digital identity. Unlike traditional models, where centralized authorities dominate, SSI empowers individuals to manage and share their identity data independently, aligning with the decentralized ethos of Web3. SSI allows users to have control over their identity data, deciding what to share and with whom, thereby ensuring privacy, security, and trust in digital interactions.
Despite the transformative potential of Web3 technologies, public awareness and adoption remain limited. Most people interact with centralized platforms daily, often without considering the underlying technologies. The concept of SSI represents a major leap forward, addressing critical issues such as privacy, security, and control, which are not fully resolved in the current digital landscape. As one of the most significant applications of Web3, SSI is positioned to be a critical driver of broader Web3 adoption, with vast potential for impact across various sectors.
As Web3 progresses toward widespread adoption, SSI emerges as a critical infrastructure element, bridging the gap between Web2 and Web3. The article explores how SSI not only enhances trust, security, and interoperability in decentralized ecosystems but also holds significant commercial potential. By enabling user-controlled digital identities, SSI opens new opportunities for businesses, ranging from improved customer privacy to more secure and efficient identity verification processes.
Concepts and Historical Evolution
What is Identity and Traditional Identity Systems
Identity refers to the characteristics, traits, or information that uniquely define an individual, entity, or concept. Historically, identity verification has been managed by centralized entities such as governments and corporations. For example, government-issued IDs (like passports and driver’s licenses) and corporate identity systems (employee badges) have been the standard methods for proving one's identity. These systems rely heavily on centralized databases where personal information is stored, controlled, and verified by the issuing authorities.
With the advent of the digital age, identity management evolved from paper-based systems to digital platforms. To utilize internet services, users must often register and remember a variety of passwords. Federated identity models such as OAuth and SAML were introduced to simplify identity verification across multiple platforms. These models allowed users to authenticate on various services using a single set of credentials, typically managed by a third party like Google or Facebook. While these systems improved convenience, they still relied on centralized control and presented similar risks of privacy invasion and data breaches.
Problems with Centralized Systems
Centralized identity systems come with significant challenges:
Privacy Concerns: Individuals have little control over how their personal data is stored, shared, or used by these centralized authorities.
Data Breaches: Centralized databases are prime targets for hackers, leading to massive data breaches where millions of personal records can be stolen.
Identity Theft: The concentration of personal information in centralized systems makes them vulnerable to identity theft, where malicious actors can steal someone’s identity and use it for fraudulent activities.
Lack of User Control: Users often cannot control or even access the full extent of their data stored in these systems, leading to a lack of transparency and trust.
What is SSI?
SSI is a decentralized approach to digital identity where individuals own and control their personal data without relying on centralized authorities. In an SSI system, users can create and manage their digital identities, share verifiable credentials selectively, and interact with digital services without the need for intermediaries.
The rise of SSI has been facilitated by foundational technologies such as blockchain and cryptography. Blockchain provides a decentralized, immutable ledger where identity transactions can be recorded securely and transparently without the need for a central authority. Cryptographic techniques, particularly public-key cryptography, enable users to create secure, verifiable credentials that can be shared without exposing the underlying personal data.
Blockchain technology, as the backbone of Web3, ensures that SSI systems are decentralized, trustless, and secure. Each identity transaction or credential issuance is recorded on a blockchain, providing a tamper-proof history that can be verified independently. This decentralized approach eliminates the risks associated with centralized identity management, such as single points of failure and data breaches.
Evolution of SSI in Web3
The journey towards SSI in the Web3 ecosystem has been marked by continuous innovation, starting from simple decentralized wallets and gradually evolving into robust identity management systems. This evolution underscores the critical need for secure, user-controlled digital identities as the world increasingly moves towards decentralization.
a. Decentralized Wallets: The Foundation of Web3 Identity
SSI’s journey within Web3 began with the widespread use of blockchain wallets. Initially, Web3 users engaged with decentralized ecosystems using wallet addresses, which acted as their anonymous digital identity. While wallets provide a way to manage digital assets, they fall short in offering a comprehensive solution for identity management. Wallets are limited to controlling cryptocurrencies or NFTs but do not inherently allow users to verify identity attributes.
b. Decentralized Identifiers (DIDs): Enhancing Identity Control
As Web3 projects evolved, DIDs began to emerge as a more robust solution for identity. Unlike wallet addresses, which are pseudonymous and primarily focused on asset management, DIDs enable users to create verifiable and portable digital identities. This allows users to interact with multiple services (e.g., dApps, DeFi platforms, NFT marketplaces) while maintaining control over their personal information.
The Ethereum Name Service (ENS) is a great example of a Web3 solution that transitions from wallet addresses to more human-readable DIDs. ENS allows users to map their Ethereum wallet addresses to readable names like “alice.eth,” making identity and asset management more accessible.
c. SSI: The Comprehensive Solution
The next stage in this evolution is the transition from DIDs to a full SSI framework. While DIDs allow users to control their digital identity, SSI adds layers of verifiable credentials, Zero-Knowledge Proofs (ZKPs), and more to create a comprehensive digital identity system that spans both Web2 and Web3. The introduction of verifiable credentials adds a layer of trust and security to DIDs by allowing users to present cryptographically signed claims about their identity. These credentials can be verified without relying on a central authority, ensuring privacy and security. This technology enhances privacy by allowing users to share only the information necessary for a given interaction while keeping other details private—a crucial feature in a world increasingly concerned with data security.
SSI is particularly useful in bridging Web2 and Web3. For example, someone could log into a Web3 dApp using a DID, present a verifiable credential that proves they are a verified individual, and interact with the platform securely and privately. Over time, SSI will play a critical role in improving user experiences in both traditional and decentralized ecosystems.
Key Technologies and Mechanisms in SSI
SSI represents a major leap forward in how we manage and control our digital identities. It relies on several core technologies that provide security, privacy, and decentralization, all of which enable individuals to own and manage their identity data without depending on centralized entities. To bring the concept of SSI to life, let’s explore its key technologies, along with real-world Web3 projects illustrating their application.
Several core technologies underpin Self-Sovereign Identity:
a. Encryption and Distributed Ledger Technology (DLT)
Encryption and DLT are the foundation of SSI, ensuring that digital identities are securely managed and transactions are immutably recorded. Distributed Ledger Technology, particularly blockchain, offers decentralized, tamper-proof systems for recording identity transactions. This ensures data transparency and prevents any single entity from modifying or tampering with identity data.
Encryption: It encrypts sensitive identity data, ensuring that only authorized parties can access it. Techniques like asymmetric encryption (public/private key pairs) are commonly used to ensure privacy.
DLT: Blockchain's distributed ledger technology provides a decentralized infrastructure that records and verifies identity credentials, preventing unauthorized changes.
b. Decentralized Key Management System (DKMS)
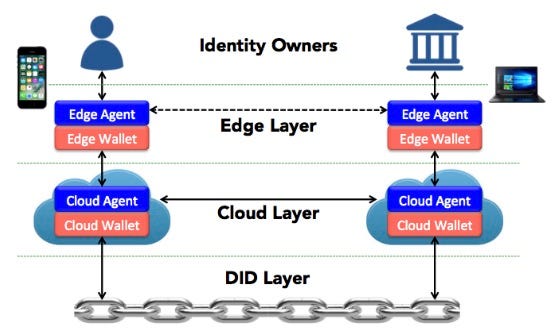
The Decentralized Key Management System (DKMS) is the main interface for users to interact with self-sovereign identity. In addition to connecting with the underlying DID, DKMS also handles tasks like credential storage and private key backup. DKMS can be divided into three sub-layers: DID Layer, Cloud Layer and Edge Layer.
DKMS Architecture
source:DKMS (Decentralized Key Management System) Design and Architecture V3
The DID layer is the core foundation where DIDs are registered and resolved on distributed ledgers. Above it, the cloud layer hosts server-side agents and wallets that facilitate secure, encrypted communication between the DID layer and the edge layer. This enables the exchange and verification of DIDs, public keys, and verifiable credentials. The edge layer comprises local devices, agents, and wallets managed directly by identity owners, where most private keys are generated and key management operations are performed.
c. Decentralized Identifiers (DIDs)
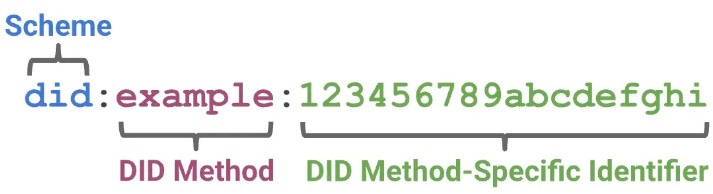
Decentralized Identifiers (DIDs) are perhaps the most crucial component of SSI , enabling secure connections and verifiable data exchange between entities (people, organizations, devices, etc.). A DID is a unique identifier composed of numbers and letters, mapped to a DID Document on a specific ledger.They are responsible for writing and reading identities on decentralized ledgers, with clear definitions for the identifier's format and resolution methods.
A simple example of a decentralized identifier (DID)
DID Methods: These are strings within the DID that determine how each DID is resolved. Each ledger has its own DID Method, which corresponds to the creation and resolution rules of the DID Document on that ledger. For example, a DID registered on Ethereum might look like did:eth:12345. DID Methods need to be registered with the W3C to be recognized by resolvers.
DID Document: Decentralized ledgers can be thought of as key-value databases, where the DID serves as the key and the corresponding DID Document as the value. A DID Document includes the public key representing the identity, verification protocols, and service endpoints that interact with the identity.
DID Resolver: This assists higher-level protocols in querying DID Documents. Resolvers can parse different DID Methods and return the results to the upper layers, which do not need to handle the complexities of document resolution. The Decentralized Identity Foundation (DIF) has developed a Universal Resolver to handle various DID Methods, which can be extended as new methods are registered.
d. Verifiable Credentials (VCs)
The main objective of Verifiable Credentials is to replace all physical credentials. VCs are digital credentials with a cryptographic foundation that are applicable to various applications. They provide a perfect scenario in which the user has complete control over their identity.
DIDs by themselves do not carry inherent trust, similar to an IP address. Their value lies in their ability to resolve into a DID document containing cryptographic keys and endpoints for secure communication.
To build trust, DKMS agents use verifiable credentials, which are standardized digital proofs of identity or attributes verified by third parties, like banks or educational institutions. The trust in these credentials depends on the trustworthiness of the issuer.
The Verifiable Credentials Working Group is standardizing how these credentials are formatted and digitally signed. For example, using zero-knowledge signatures allows users to prove their credentials without revealing sensitive data, maintaining privacy through "link secrets" stored in DKMS wallets.
The following diagram from the Verifiable Credentials Working Group illustrates the primary roles in the verifiable credential ecosystem and the close relationship between DIDs and verifiable credentials.
The W3C Verifiable Credentials ecosystem
Market Analysis
Market Size
a. Traditional Identity Management Market Size
The traditional Identity and Access Management (IAM) market has been a cornerstone of digital security for decades, providing solutions that help organizations manage user identities, enforce security policies, and ensure compliance with regulatory requirements. As digital transformation accelerates across industries, the demand for robust IAM solutions has grown significantly.
The traditional IAM market, valued at $12.26 billion in 2022, is expected to grow to $24.12 billion by 2026, driven by the ongoing need for secure and scalable identity management solutions in enterprise environments. The CAGR of 13.2% reflects steady growth, supported by increased adoption of cloud-based IAM, the proliferation of digital services, and heightened cybersecurity concerns.
The IAM market is dominated by several key players, including IBM, Microsoft, Oracle, and Okta. The revenue trends of these IAM giants reflect the market's overall growth and the increasing importance of digital identity management.
Below is a summary of the revenue trends for leading IAM companies:
However, traditional IAM systems face several challenges, including high implementation costs, complex integration processes, and vulnerabilities associated with centralized identity storage. These issues have prompted organizations to explore alternative solutions that can offer greater security, flexibility, and user control.
b. SSI Market Size and Potential
The SSI market is still in its early stages, it is rapidly gaining momentum as businesses, governments, and individuals recognize the benefits of this new approach.
As of 2023, the SSI market is estimated to be worth around $1.1 billion, with significant growth potential. Analysts project that the SSI market could reach $5.3 billion by 2028, expanding at a CAGR of 39.6% over the next five years . This impressive growth is driven by several factors, including increasing awareness of data privacy issues, the rise of blockchain technology, and the growing need for secure digital identities in sectors like finance, healthcare, and education.
The market dynamics between traditional IAM and SSI are evolving rapidly. While traditional IAM remains dominant in terms of current market size, the SSI market is growing at a much faster pace, indicating a potential shift in the identity management landscape.
Below is a comparative Market Analysis of SSI and Traditional IAM:
The traditional IAM market is substantial and well-established, with projections indicating continued growth due to the ongoing digital transformation and increasing cybersecurity needs. However, the rapid growth of the SSI market suggests that decentralized identity solutions are gaining traction and could potentially disrupt the traditional IAM market in the future.
The traditional IAM market, while continui ng to grow, faces challenges from emerging technologies like SSI, which offers enhanced security, privacy, and user control. As the SSI market expands, it is likely to capture a growing share of the broader identity management market, particularly in regions and sectors where data privacy is a top priority.
Market drivers for SSI
The momentum behind SSI is undeniable, driven by a combination of business efficiency and customer experience, resistance to the surveillance economy, and the Sovereign Individual Movement.
a. Business Efficiency and Customer Experience
One of the primary forces propelling the adoption of SSI is the potential for improved business efficiency and enhanced customer experience. Traditional identity and access management (IAM) systems are often plagued by inefficiencies, high costs, and security vulnerabilities. In contrast, SSI offers a more secure, cost-effective, and user-friendly alternative, making it highly attractive to businesses across various sectors.
Security and Cost Savings
Security concerns are at the forefront of why organizations are looking to SSI. In traditional IAM systems, identity data is often stored centrally, making it a prime target for cyberattacks. According to a 2023 report by Cybersecurity Ventures, global cybercrime costs are expected to reach $10.5 trillion annually by 2025 . SSI mitigates this risk by allowing individuals to store their identity data on their own devices or within decentralized networks, reducing the attack surface for hackers. This decentralized approach not only enhances security but also reduces the costs associated with data breaches, compliance with privacy regulations, and IAM system maintenance.
Market Demand from Corporations, Governments, Universities, and NGOs
The growing interest from various sectors further highlights the business efficiency benefits of SSI. Corporations see SSI as a means to streamline operations, reduce onboarding times, and improve customer trust. Governments are exploring SSI to provide citizens with secure, digital identities that can be used across multiple services, as seen in initiatives like the European Union’s eIDAS regulation, which promotes cross-border electronic identification and trust services .
Universities and NGOs are also early adopters, utilizing SSI for credential verification and secure data sharing. For instance, the MIT Media Lab has been a pioneer in exploring the use of SSI for academic credentials, enabling students to own and share their degrees without relying on third-party verification . This early-stage demand is creating new market segments and opportunities for companies specializing in SSI solutions.
b. Resistance to the Surveillance Economy
The second key driver behind the SSI momentum is the growing resistance to the surveillance economy, which is largely fueled by the Web 2.0 business model. This model is characterized by the pervasive collection, aggregation, and resale of personal data by tech giants and data brokers. In response, SSI offers a way to counteract this trend, empowering individuals and organizations to regain control over personal data.
Counteracting Surveillance Capitalism
Surveillance capitalism, a term popularized by scholar Shoshana Zuboff, describes the economic system where personal data is commodified and used to drive targeted advertising and influence behavior . SSI challenges this model by enabling individuals to control who has access to their data and under what conditions. This is particularly appealing to privacy-conscious consumers and organizations that are increasingly wary of the ethical implications of data exploitation.
Support from Governments and Privacy Advocates
Governments and privacy advocates are key supporters of SSI as a means to counter the surveillance economy. The European Union has been a leading force in this movement with the implementation of the General Data Protection Regulation (GDPR). GDPR has set a global standard for data privacy, emphasizing the importance of individual consent and control over personal data . SSI aligns perfectly with GDPR principles, making it a preferred solution for compliance.
Privacy advocates and non-profit organizations are also vocal proponents of SSI. These groups argue that the current digital identity systems contribute to the erosion of privacy and advocate for SSI as a way to protect individual freedoms. The support from these entities is crucial in driving the adoption of SSI, particularly in regions with strong privacy protection laws.
Strategic Corporate Adoption
Strategic corporations are also recognizing the benefits of SSI as a way to differentiate themselves in a market increasingly concerned with privacy. Companies that adopt SSI can position themselves as champions of user privacy, gaining the trust of consumers who are disillusioned with the traditional data economy. This shift is evident in the growing number of tech companies exploring SSI as part of their broader privacy and security strategies .
c. The Sovereign Individual Movement
The third major driver of SSI is the Sovereign Individual Movement, which advocates for maximum decentralization and individual control over personal data. This movement is inspired by the philosophy behind decentralized currencies like Bitcoin and the vision outlined in the book The Sovereign Individual by James Dale Davidson and William Rees-Mogg.
Decentralization and Individual Autonomy
At its core, the Sovereign Individual Movement is about decentralization and autonomy. Just as Bitcoin and other cryptocurrencies seek to eliminate the need for centralized financial institutions, SSI aims to eliminate the need for centralized identity authorities. This is achieved through the use of blockchain and other decentralized technologies that allow individuals to create and manage their digital identities independently.
The appeal of this approach is growing, particularly among tech-savvy individuals and communities that value privacy, freedom, and self-determination. These individuals are often early adopters of new technologies and play a crucial role in driving the adoption of SSI.
Alignment with Decentralized Finance (DeFi)
SSI is also closely aligned with the broader decentralized finance (DeFi) movement. DeFi has experienced exponential growth since its inception. According to data from DeFi Pulse, the total value locked (TVL) in DeFi protocols reached approximately $100 billion in 2023, up from just $1 billion in 2019. This explosive growth highlights the increasing demand for decentralized financial services and the trust that users are placing in these platforms .
The DeFi market size is projected to continue its rapid expansion. A report by Grand View Research estimates that the global DeFi market was valued at $13 billion in 2023 and is expected to grow at a compound annual growth rate (CAGR) of 42.5% from 2024 to 2030, reaching a market size of approximately $125 billion by 2030 . As the DeFi market expands, the need for secure, decentralized identity solutions becomes increasingly important. SSI provides a way for DeFi platforms to verify user identities without relying on centralized authorities, which aligns with the core principles of DeFi. This synergy between SSI and DeFi is expected to drive further adoption of both technologies.
Support from Ideological and Technological Communities
The Sovereign Individual Movement is supported by a growing number of ideological and technological communities that advocate for decentralized technologies. These communities see SSI as a critical component of a broader shift towards decentralization in all aspects of digital life. This support is driving innovation and investment in SSI technologies, leading to the development of new platforms and solutions that further enhance individual control over personal data.
Business Models of SSI in Web3
The business model of SSI in Web3 revolves around offering decentralized identity solutions that empower individuals to control their personal data while providing verifiable credentials for various use cases. Here's a breakdown of how SSI providers generate revenue:
Issuance of Verifiable Credentials (VCs):
Institutions issue verifiable credentials that confirm identity, education, or certifications, recorded on a blockchain for verification. These entities charge for credential issuance and management. Dock allows businesses to create and issue verifiable credentials, with companies paying for these services to integrate decentralized credentials into their systems.
Credential Verification Services:
Verifiable credentials can be checked by third-party entities (e.g., employers) to verify identity or qualifications. Verification services charge fees per verification request. Civic offers decentralized identity verification, with businesses paying for these services to ensure secure user authentication on their platforms.
Identity Management Platforms (Subscription-based):
SSI platforms offer identity management tools, where users securely manage private keys, DIDs, and credentials. Enterprises can subscribe to premium services for enhanced management and integration. Serto provides subscription-based identity management tools, helping enterprises handle decentralized identities within Web3 ecosystems.
Consulting and Integration Services:
SSI solution providers offer consulting and integration to companies that want to adopt decentralized identity into their infrastructure, charging for custom development and implementation. Jolocom provides SSI integration services, helping enterprises incorporate decentralized identity management into their workflows, with revenue from consultation and development.
Marketplace for Verified Identities:
Decentralized marketplaces can allow individuals to trade or interact based on trusted identities. SSI platforms may charge transaction fees or commissions on exchanges involving verified identities. KILT Protocol enables tokenized identities, allowing participants to verify and exchange credentials, generating income through fees for identity verification.
Privacy-enhancing Tools:
SSI solutions enhance user privacy, using methods like zero-knowledge proofs. Platforms charge for privacy tools and secure data sharing solutions, which help prevent exposure of unnecessary information. Ocean Protocol allows users to control and monetize their data securely, with SSI and privacy tools integrated, generating fees for data transactions.
Partnerships with dApps:
SSI systems integrated with decentralized applications (dApps) in DeFi, NFTs, and other Web3 platforms enable secure, trusted interactions. SSI providers may charge fees for integration and value-added features. Projects like Aave and Uniswap have begun exploring how SSI could be used for identity verification without compromising user privacy. For instance, integrating verifiable credentials into DeFi protocols could allow users to prove compliance with regulations (e.g., age or jurisdiction) without revealing personal details.
Investment in SSI
The SSI market has garnered increasing interest from investors due to its potential to transform digital identity management. As regulatory frameworks evolve and digital security becomes more paramount, SSI's potential has driven significant investment activity. Over the past five years, the SSI market has seen cumulative investments exceed $300 million. Investment in SSI has shown a compound annual growth rate of approximately 25% since 2018, with a notable surge in 2020 and 2021 due to heightened interest in decentralized solutions during the global pandemic. This growth is driven by both venture capital and strategic corporate investments.
As we delve deeper into the dynamics of this burgeoning market, several key investment trends and notable funding rounds provide insight into how SSI is shaping the future of digital identity.
a. Major Players in SSI Funding
Early-Stage Investments and Startups: One of the most prominent trends within the SSI market is the concentration of investments in early-stage startups. These companies are at the forefront of developing foundational technologies that enable decentralized identity management. Venture capital firms, recognizing the disruptive potential of SSI, have been particularly active in funding these startups. The focus of these investments is often on building decentralized identity networks, blockchain-based identity solutions, and the necessary infrastructure to support these innovations.
Strategic Investments by Established Companies: In addition to the momentum among startups, large technology firms and financial institutions are increasingly making strategic investments in SSI. These investments are not just financial; they also reflect a broader strategy to integrate SSI technologies into existing platforms. By doing so, these companies aim to enhance their service offerings with decentralized identity capabilities, positioning themselves as leaders in the digital identity space.
Government and Institutional Funding: Another significant trend is the involvement of governments and international organizations in funding SSI initiatives. Through grants and public-private partnerships, these entities are contributing to the growth of the SSI ecosystem. This type of funding is often directed towards promoting the adoption of SSI in key areas such as digital government services, healthcare, and financial inclusion, highlighting the broader societal impact of SSI technologies.
As these trends illustrate, the investment landscape for SSI is both dynamic and diverse, with a wide range of players contributing to the development and adoption of SSI technologies.
b. Notable Funding Rounds and Investments
To better understand the momentum behind SSI, it's essential to look at some of the most notable funding rounds and investments within the sector. These examples, which include blockchain-based SSI projects, underscore the strong belief in SSI’s potential to redefine digital identity management on a global scale.
These investments highlight the broad interest and diverse approaches to building and implementing SSI solutions. From blockchain-based identity verification tools like Civic to platforms designed to comply with stringent European regulations like Jolocom, the variety and scale of investments demonstrate a strong and growing belief in SSI’s potential to transform how digital identities are managed globally.
As SSI continues to evolve, the ongoing influx of capital will likely drive further innovation and adoption, solidifying its role as a cornerstone of the digital identity landscape in the years to come.
Current Situation and Adoption of SSI in Web3
SSI has emerged as a critical technology in the Web3 ecosystem. Web3, with its focus on decentralization, transparency, and user autonomy, provides an ideal environment for the development and adoption of SSI. However, despite its potential, SSI in Web3 still faces a variety of technical, regulatory, and adoption challenges. Existing Decentralized Identity Platforms and Initiatives
Ethereum-based SSI Projects:
uPort: One of the early SSI solutions built on Ethereum, uPort allows users to create and manage their digital identities through blockchain technology. Users can store verifiable credentials, share them with other services, and authenticate themselves on dApps using their decentralized identity.
BrightID: Focuses on enabling decentralized identity verification for anti-sybil mechanisms. BrightID creates a unique identifier for users without exposing personal information, helping dApps prevent fraudulent accounts in decentralized networks.
Internet Computer Protocol (ICP) - Internet Identity (II):
Internet Identity allows users to authenticate themselves across decentralized applications (dApps) on the ICP network using cryptographic keys, without the need for passwords. This decentralized authentication system aligns closely with the SSI model, giving users control over their digital identity without relying on a centralized identity provider.
Polkadot and Parity Technologies - DID Framework:
Polkadot integrates a decentralized identifier framework for Web3 services. The DID module in Polkadot allows users to create portable and self-sovereign identities that can be used across multiple blockchain networks.
Solana's Civic:
Civic builds on Solana’s fast and scalable blockchain, offering decentralized identity management services. The platform enables users to prove their identity while maintaining privacy, and its application ranges from login services to anti-fraud mechanisms within Web3 ecosystems.
The Most Shaped SSI Design - II
The Internet Identity (II) system in the Internet Computer Protocol (ICP) represents a novel approach to decentralized identity management, integrating several key principles and technologies aligned with SSI. Therefore, this article will briefly introduce the ICP II identity system to brief the current development status of II.
Key Technology of ICP Internet Identity:
Internet Identity principal
In Internet Identity (II) on ICP, a “principal” is a unique, cryptographic identifier generated when a user authenticates through methods like WebAuthn. This principal, tied to the user's public keys, serves as their identity across dApps on the Internet Computer, similar to how DIDs function in decentralized systems.
Authentication Through Cryptographic Signatures
II uses WebAuthn, an open standard supported by most modern browsers, for device-based authentication. Instead of usernames and passwords, users authenticate via cryptographic key pairs stored on hardware devices such as security keys, fingerprint readers, or FaceID.
The device generates a public-private key pair, where the public key is stored in an identity anchor, and the private key never leaves the user's device.
This cryptographic signature is validated against the stored public key on the blockchain to verify the user's identity.
Users can register multiple WebAuthn devices under the same identity anchor. This functionality serves as a backup mechanism. If a user loses one device, they can use another registered device to authenticate.
Delegation of Identity
Users in the II system can delegate their identities to devices they trust. For instance, a user can authorize their mobile phone or laptop to act on their behalf. This delegation is secured by cryptographic proofs and can be revoked at any time.
This method ensures seamless access to decentralized applications (dApps) on ICP, where users don’t need to manually re-authenticate each time they switch between devices.
The use of hardware-backed cryptographic keys ensures that Internet Identity provides high levels of security, making it resistant to phishing, hacking, and other credential-based attacks.
Users control what personal information is shared with applications. The ability to authenticate without revealing sensitive information makes the system ideal for privacy-conscious users.
The Internet Identity system allows users to authenticate themselves on the Internet Computer platform and interact with dApps without needing to create multiple accounts or manage different credentials. This approach is in line with the principles of SSI, where the user remains in control of their identity across applications. For instance, OpenChat (a decentralized chat application built on ICP) allows users to sign in with Internet Identity. Once authenticated, users can chat without needing to create a separate account for the platform, maintaining a single identity across the dApp.
Adoption Challenges
Despite significant progress, SSI adoption in Web3 faces several hurdles:
Technical Challenges
Interoperability: One of the main technical challenges is ensuring interoperability across different blockchains and Web3 platforms. Different platforms use their own DIDs and verifiable credential standards, which can hinder seamless cross-platform identity management.For instance, ICP II works seamlessly within the ICP ecosystem, its usage outside ICP or in cross-chain environments may be limited until it gains broader support in other decentralized ecosystems(ICP is developing the chain fusion technology helps to solve this issue).
Scalability: The decentralized nature of SSI often leads to scalability issues, particularly in networks with a high volume of transactions. Blockchain networks need to manage the growing number of identity verification requests, which can introduce latency.
User Experience: SSI requires users to manage cryptographic keys, which can be cumbersome. The technical complexity may act as a barrier to entry for non-tech-savvy users, limiting mass adoption.
Regulatory Challenges
Regulatory Uncertainty: Government regulations surrounding decentralized identity are still in their early stages. Different countries have varying stances on privacy, data control, and identity verification processes. For instance, the European Union's GDPR regulations conflict with some blockchain-based SSI solutions that emphasize immutability, making it difficult to reconcile privacy rights with decentralized data storage.
Compliance with Existing Laws: Decentralized identity systems need to comply with anti-money laundering (AML) and know-your-customer (KYC) regulations, especially in DeFi applications. This poses challenges for projects aiming to preserve user privacy while fulfilling legal obligations.
User Adoption Challenges
Lack of Awareness: Many users are not familiar with the concept of SSI or its advantages over centralized identity systems. Educating users on the benefits of controlling their own identities will be critical for broader adoption.
Trust: Trust in decentralized systems remains an issue for some users, especially when compared to the perceived security of established, centralized institutions. There is a need for SSI systems to prove their reliability and security.
Conclusion
SSI is poised to become a cornerstone of the Web3 ecosystem, providing the trust, privacy, and user control necessary for a decentralized digital future. By replacing traditional, centralized identity systems, SSI offers a more secure, interoperable, and privacy-preserving model that aligns with the decentralized ethos of Web3. As public awareness and interaction with Web3 technologies grow, SSI is likely to emerge as one of the most significant applications driving Web3 adoption. Its future prospects are vast, with the potential to reshape how we manage and protect our digital identities in a rapidly evolving digital landscape.
References
Cameron, Kim. 2005. “The Laws of Identity.” Kim Cameron’s Identity Weblog. www.identityblog.com/?p=352.
https://medium.com/taipei-ethereum-meetup/intro-to-ssi-e643cd7300fa
Christopher Allen. 2016. “The Path to Self-Sovereign Identity” https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/ThePathToSelf-SovereignIdentity.md
Cybersecurity Ventures. (2023). Cybercrime to Cost the World $10.5 Trillion Annually by 2025. Retrieved from https://cybersecurityventures.com
European Commission. (2021). eIDAS Regulation: Ensuring Trust and Security in the Digital World. Retrieved from https://ec.europa.eu/digital-strategy.
MIT Media Lab. (2022). Exploring Self-Sovereign Identity for Academic Credentials. Retrieved from https://www.media.mit.edu
Mordor Intelligence. (2022). Identity and Access Management Market - Growth, Trends, COVID-19 Impact, and Forecasts (2021 - 2026). Retrieved from
https://www.mordorintelligence.com
Zuboff, S. (2019). The Age of Surveillance Capitalism: The Fight for a Human Future at the New Frontier of Power. PublicAffairs.
European Commission. (2018). General Data Protection Regulation (GDPR). Retrieved from https://ec.europa.eu/info/law/law-topic/data-protection/data-protection-eu_en.
Gartner. (2023). Gartner Forecasts Worldwide Information Security Spending to Exceed $150 Billion in 2023. Retrieved from https://www.gartner.com
Davidson, J.D., & Rees-Mogg, W. (1997). The Sovereign Individual: Mastering the Transition to the Information Age. Simon & Schuster.
DeFi Pulse. (2023). DeFi Market Overview. Retrieved from https://defipulse.com
Grand View Research. (2023). Decentralized Finance (DeFi) Market Size, Share & Trends Analysis Report By Component, By Application, By Region, And Segment Forecasts, 2024 - 2030. Retrieved from https://www.grandviewresearch.com
Messari. (2023). The DeFi Report: Market Analysis & Ecosystem Overview. Retrieved from https://messari.io
W3C. (2024). “Decentralized Identifiers (DIDs) v1.1Core architecture, data model, and representations” https://w3c.github.io/did-core/
Kyle Den Hartog. (2018). “DKMS (Decentralized Key Management System) Design and Architecture V3”. https://github.com/hyperledger-archives/indy-sdk/blob/